Master EIGRP for a successful Cisco certification journey
Before starting Route-Filtering in EIGRP candidate should know about ACL, Prefix-list & route-map.
When we do a discussion about Route-Filtering so we are playing with control plane, in Route-Filtering we filter the control plane information.
So in EIGRP we can use both IN and OUT direction to filter the routes, it means we can control the routes in (IN Direction) & in (OUT Direction) also.
To put the filtering for control plane we use Distribute List with ACL, Prefix-list and Route-map also.
So let’s start filtering using Standard ACL
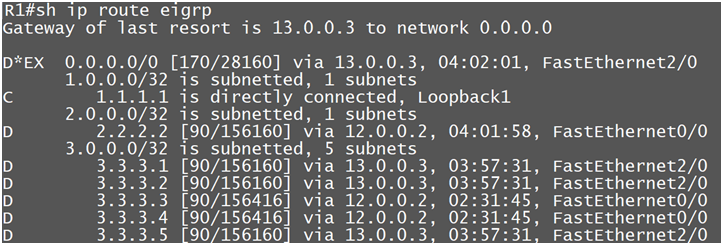
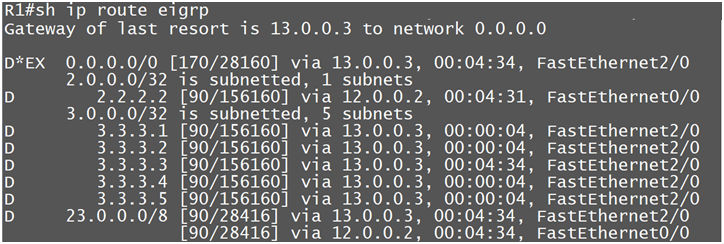
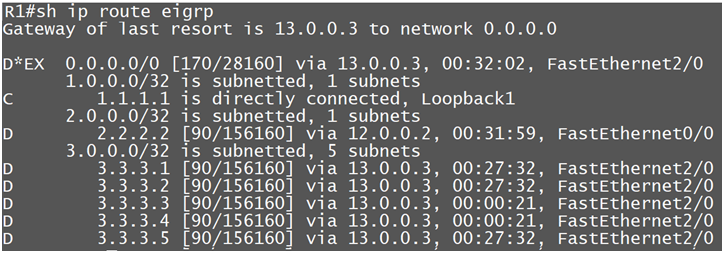
So here R1 is getting few prefixes from R3 as best
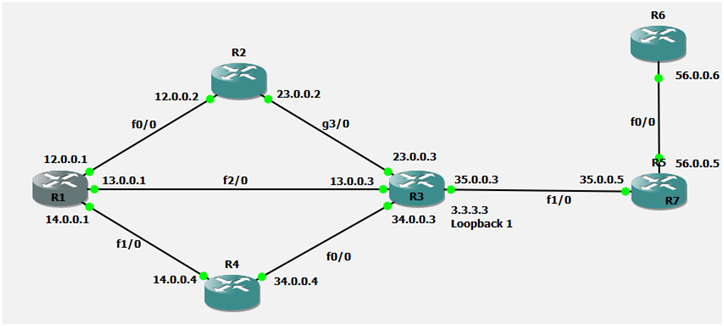
Now we will filter 3.3.3.3 and 3.3.3.4 prefix from R3(13.0.0.03), and after the filtering these 2 routes should get via other router.
*R1(config)#access-list 10 deny host 3.3.3.3
*R1(config)#access-list 10 deny host 3.3.3.4
*R1(config)#access-list 10 permit any
*R1(config)#router eigrp 10
*R1(config-router)#distribute-list 10 in fastEthernet 2/0
We need to specify the interface also on which we want to filter the traffic, if we don’t take this interface so it will filter on all the interfaces and we will lost the connectivity from all the interfaces.
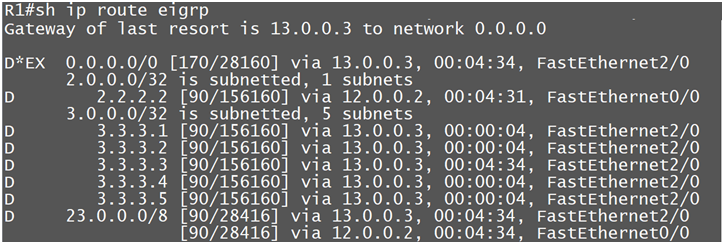
Now we are learning the routes from other Router R2
Now let’s do filtering using Extended ACL
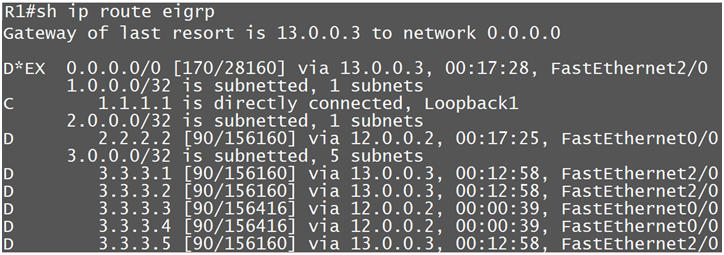
In Extended ACL we have option to match source and destination prefix, so in this case the next-hop IP(13.0.0.3) will act as Source address & the route/prefix(3.3.3.3 & 3.3.3.4) will act as destination address, accordingly we will configure our ACL
*R1(config)#access-list 101 deny ip host 13.0.0.03 host 3.3.3.3
*R1(config)#access-list 101 deny ip host 13.0.0.03 host 3.3.3.4
*R1(config)#access-list 101 permit ip any any
*R1(config)#router eigrp 10
*R1(config-router)#distribute-list 101 in fastEthernet 2/0
*R1(config-router)#exit
Now again we are learning the routes from R2.
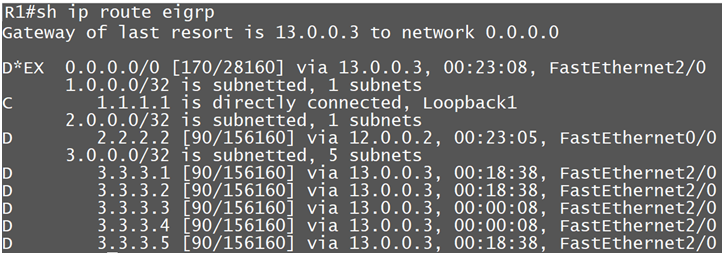
Now let’s filter the routes using Prefix-list
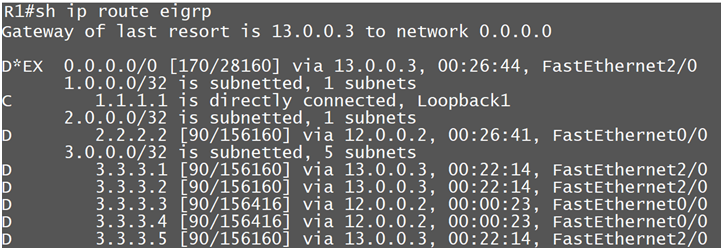
In Prefix-list we match the prefix and length also, in our case the routes we have are having /32 CIDR value
*R1(config)#ip prefix-list Filter deny
*R1(config)#ip prefix-list Filter deny 3.3.3.3/32
*R1(config)#ip prefix-list Filter deny 3.3.3.4/32
*R1(config)#ip prefix-list Filter permit 0.0.0.0/0 le 32
*R1(config)#router eigrp 10
*R1(config-router)#distribute-list prefix Filter in fastethernet 2/0
*R1(config-router)#exit
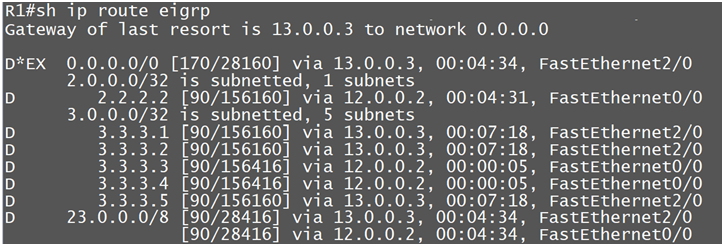
Now we are getting prefixes from other router R2
Now let’s use Route-map to filter the routes, when we use route-map we need to call ACL or Prefix-list in route-map
Whenever we use route-map, we always configure ACL or prefix-list with action permit and route-map takes the decision of deny.
So as of now we are getting routes from Router R3
We will use here ACL and Prefix-list in different seq number of route-map to deny the routes.
*R1(config)#access-list 90 permit host 3.3.3.3
*R1(config)#ip prefix-list 90 permit 3.3.3.4/32
*R1(config)#route-map filter deny 10
*R1(config-route-map)#match ip address 90
*R1(config-route-map)#exit
*R1(config)#route-map filter deny 20
*R1(config-route-map)#match ip address prefix-list 90
*R1(config-route-map)#exit
*R1(config)#route-map filter permit 30
*R1(config-route-map)#exit
*R1(config)#router eigrp 10
*R1(config-router)#distribute-list route-map filter in fastethernet 2/0
Here again after this filtering we are getting the prefixes from other Router R2